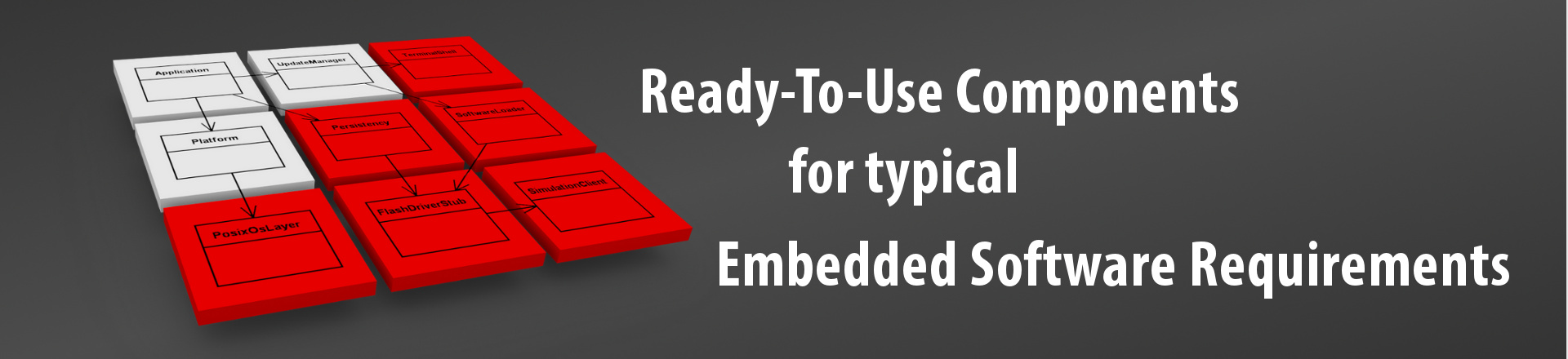
There is probably no embedded software application that does not need checksum and hash algorithms. They are used to check data integrity and authentication and are applied in many different contexts:
- data transmission, i. e. protocol implementations
- integrity check of the software before it is being started by a bootloader
- authentication when changing configuration data
- ...
The redBlocks Component Library includes classes that provide software implementations for many common checksum and hash algorithms (e. g. CRC). For optimum performance on the deployed platform, the classes are configured during compile time.